ABOUT
Why Monitor Firmware?Firmware is Everywhere
Firmware is a critical part of every device – it sits at the heart of every server, storage device, router, workstation, printer, SCADA device and IoT device on your network. It is also deep inside critical infrastructure such as refineries, power plants, and nuclear plants.
Firmware controls functions above it like a master puppeteer. In IoT and OT devices, firmware may be the only code on the system. When compromised, firmware can wreak havoc, potentially shutting down operations or taking out critical infrastructure.
Why is Firmware an Attractive Target?
Firmware is stealthy and difficult to eliminate once compromised. If you control the firmware, you can steal data, shut down critical infrastructure systems, and basically do anything you want to that machine.
Firmware attacks are persistent and stealthy, meaning they are hard to find and will remain in place even after a reboot or drive swap. Even a breach into a single coffee pot in the breakroom can lead to disruptions in entire IT systems or critical operational technology such as weapon systems, flight control systems, water purification systems, nuclear systems and more.
Firmware Attacks are Persistent
Firmware attacks can persist even after a reboot, OS reload or hard drive swap. Normal incident response remediation will not eliminate a firmware threat.
Firmware Attacks are Stealthy
Firmware sits below the OS where traditional malware detection tools have zero visibility. Attackers can get in, then lie in wait for months planning their attack without ever being noticed.
Firmware Attackers Can Take System Control
If you control the firmware, you control the system and can bypass existing security measures to take complete control.
Firmware is Extremely Vulnerable
According to Microsoft, 83% of enterprises surveyed have experienced at least one firmware attack during the past two years, but less than a third of security budgets are dedicated to protecting firmware.
Firmware is vulnerable because existing security tools provide zero visibility into the firmware layer. Trapezoid is the only commercially available, device-agnostic solution that delivers continuous visibility below the OS by monitoring, detecting and alerting for compromised firmware and device integrity.
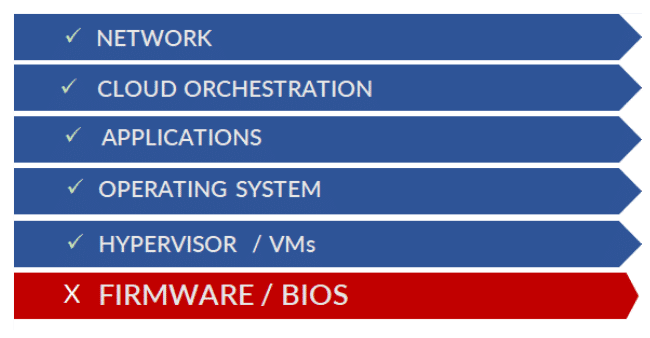
Traditional security tools protect above the OS but only Trapezoid covers vulnerabilities below the operating system (VBOS)
“There are two types of companies – those who have experienced a firmware attack, and those who have experienced a firmware attack but don’t know it.”
Azim Shafqat, ICG and former managing VP at Gartner
Take the next step