USE CASES
Operational HygieneGood Operational Hygiene is Good Security, Which is Good Compliance
Without Trapezoid FIVE, you have zero visibility into a critical layer of every device on your network. This means you cannot set best practices for known and unknown vulnerable firmware. Nor can you operationally manage firmware vulnerabilities and related threats to your operations. Without this visibility, you cannot improve your security posture below the OS.
In short, you cannot manage what you cannot see. And if you cannot see it, you cannot improve upon or measure your performance.

You Cannot Improve your Cybersecurity Posture Without Visibility into your Firmware
It is no secret that bad actors are focusing on firmware as a threat vector. They exploit existing vulnerabilities and even develop malicious code targeting the firmware itself. These types of exploits are not visible to traditional security tools. So you are not seeing a swath of potential vulnerabilities in your infrastructure.
Best practice assumes a “zero-trust” security posture for every device on your network. Trapezoid FIVE allows you to operationalize how you manage vulnerabilities below the OS. It gives you real time events and lets you set metrics to improve the security of your firmware environment.
Trapezoid FIVE Gives you Operational Visibility into Your Enterprise
Deploy Trapezoid FIVE and gain real-time visibility to firmware and device integrity. Now you can manage the state of your firmware across device manufacturers and types – be it IT, OT or IoT. And set organizational standards to improve your security posture below the OS.
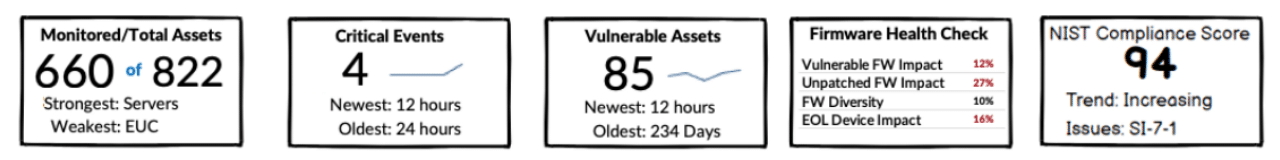
Monitored Total Assets
How many devices do you have? How many are you monitoring below the OS? How many are you not monitoring and why? Trapezoid FIVE lets you track these important metrics to meet your security and compliance goals.
Critical Events
Has the firmware on a device changed? Are there known vulnerabilities in a particular firmware version? Did someone alter critical configuration setting? Was a piece of hardware swapped out? Trapezoid FIVE alerts you to critical events impacting device integrity below the OS.
Firmware Healthcheck
Firmware can be vulnerable, unpatched or end-of-life. Each of these states represents a potential risk to your infrastructure. Trapezoid FIVE tracks these states for the devices it monitors.
Vulnerable Assets
Trapezoid FIVE checks OEM, NVD and 3rd Party research feeds for vulnerabilities, and maps these to devices on your network. It also flags end-of-live devices. It tags these as vulnerable and displays them on one screen so you can see which need attention.
NIST Compliance Score
Trapezoid FIVE covers all the NIST SP 800-53 firmware-related controls. It maps the relevant controls for each device. It also provides a total NIST firmware compliance score across device types. This gives you immediate insight into your compliance posture.