USE CASES
Firmware Incident ResponseYou Can’t Respond to an Incident You Don’t Know About
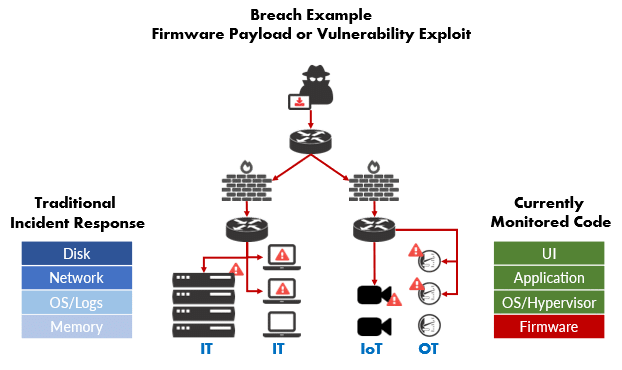
Without visibility into your firmware environment, you cannot manage your firmware vulnerabilities. That means you have no meaningful integrity data about devices on your network to analyze for indicators of compromise.
Traditional incident response forensic analysis methods do not work for evaluating firmware. They focus on data gathered at or above the operating system. Looking at memory, disk, logs, and network traffic will not tell you what is happening below the OS. To really understand firmware and device integrity, you need a different set of metrics altogether.

A Server-Based, IT-Centric View of Firmware Security is Insufficent
Every device type is different. You cannot possibly develop a taxonomy for every make and model in the world. For example, x86 servers are totally different from routers. Routers are totally different from Smart TVs. And etc. Addressing vulnerabilities below the OS through device classification does not scale.
To overcome this challenge, the Trapezoid team took a new approach. Trapezoid FIVE captures relevant integrity data from a deviceto establish its behavior. Every time we query a device, we create an evidence record. This data establishes the state of that device at a specific moment in time. We track this data over time to model the individual device’s behavior. We can then compare the current integrity data against prior data for that device and that of similar devices as a group.
Behavior-Based Device Monitoring Across the Trapezoid Quadrants Detects Indicators of Compromise
As Trapezoid FIVE gathers integrity data from a device, it looks for deviations from the device’s baseline behavior. It analyses the device data across the Trapezoid(r) Quadrants of Integrity for indicators of compromise. Those quadrants are Hardware, Software (firmware), Configuration, and Operational Metrics.
- A new piece of hardware is a sign that someone had physical access to a device. But was it authorized? If not, is the device compromised?
- Does the device have any artifacts that validate the integrity of its firmware? A firmware update that does not match the manufacturer’s measurements could be either an operations or security issue.
- Some firmware attacks can only be detected by changes in configuration.
- A spike in power or temperature could be operational metrics that can be an early warning sign of something worse.
- Anomalous behavior in any of the Quadrants of Integrity is suspect and may result in an alert.
The platform also continuously checks against the vulnerability research loaded into Trapezoid FIVE. This research includes OEM known good values, the National Vulnerability Database, independent research sources, plus any customer’s own research they want to include.
Make Real-time Incident Response Remediation Decisions with Confidence

With Trapezoid FIVE, you can determine indictors of compromise, model device behavior, utilize best-in-class research to receive intelligent alerts, and forensically investigate below the OS. Armed with the Trapezoid FIVE platform, for the first time you can make real-time remediation decisions.