USE CASES
ComplianceEvery Major Cybersecurity Framework in the World Requires You to Continuously Monitor Firmware
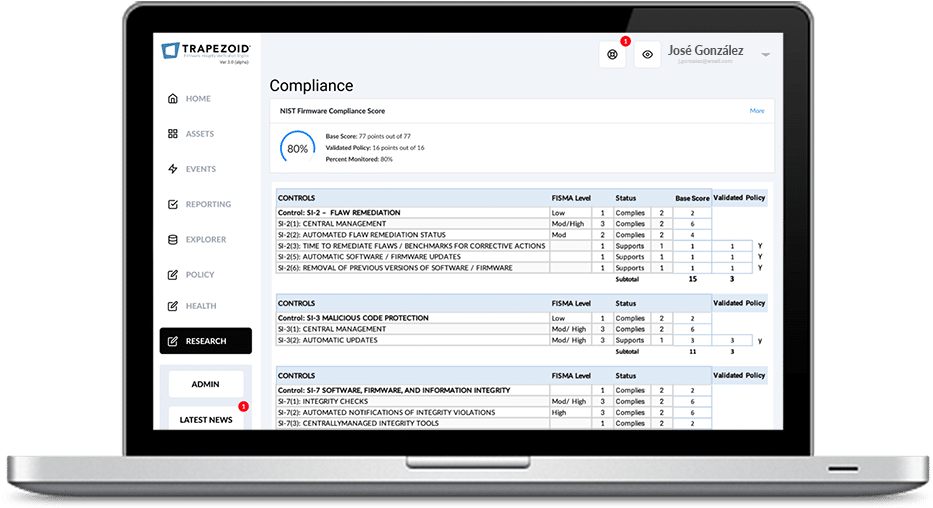
Many companies contact Trapezoid because they have failed to meet NIST SP 800-53 SI-7 controls. These controls require the continuous monitoring of firmware for indicators of compromise. This is not unique to NIST & FISMA.
Lack of visibility into this layer of security means you cannot detect any changes below the operating system. As such, you cannot analyze those changes to determine if they should be alerted or acted upon.

Frameworks Requiring Continuous Firmware Monitoring
All Federal Civilian and Defense Agencies Must All be NIST Compliant
NIST Cybersecurity Framework (PR.DS-6) SP 800-53 (SI-7)
FARs and DFARS - Federal Government Contractor Requirements
DFARS clause 252.204-7012 - Safeguarding Covered Defense Information and Cyber Incident Reporting
CMMC - Defense Contractor Certification
GDPR - failure to patch firmware could lead to breach and material fines
HHS CMS ARS 3.1 (SI-7)
HITRUST CSF - Control Reference: 10.c - Control of Internal Processing
HIPAA - 45 CFR Part 164.306(a)(2) - Protect against “reasonably anticipated" threats includes firmware per HHS comments
BANKING - PCI-DSS - definition of malware includes firmware
FINANCIAL SERVICES - Sector Cybersecurity Profile (PR.DS-6)
Achieve your Cybersecurity Compliance Requirements for Firmware with Trapezoid FIVE
Deploy Trapezoid FIVE and gain immediate insights into the firmware threat vector. Get actionable data mapped to every NIST firmware-related control by device in real-time. Produce reports on-the-fly for your auditors proving you meeting your firmware device monitoring compliance requirements.